Archive for February, 2015
Product Review: Aegis Padlock SSD 3.0
I find myself having to move sensitive information such as certificates, key material and configuration files around quite a bit, and it’s vital that this sort of thing stay encrypted.
Since the Truecrypt fiasco, I’ve been looking for something that is simple and cross-platform, and not dependent on a flaky development team that that has already pulled out. When I realized there is a new USB 3.0 version of the Aegis Padlock drive from Apricorn out, I thought I’d give it a try.
Published specs:
| Data Transfer Rate | USB 3.0 – up to 200 MB/sec | *To acheive these data transfer speeds, your computer’s internal drive must be solid state. In the case of your computer having a hard drive, the speed will be limited by your internal HDD |
|---|---|
| Power Supply | 100% Bus Powered |
| Buffersize | 8MB |
| Interface | USB 3.0 |
| Average seek time | 0.1 ms Access Time |
| Shock – operating | 1500G/0.5ms | Virtually shock and vibration resistant |
| Dimensions | 2.5 in x 3.3 in x 0.55 in | 64.5 mm x 83.5 mm x 14mm |
| Warranty | 3 Year Limited |
| Approvals | FC CE | FIPS 140-2 Level 2 Validated |
| Certification Policies | Click here for Security Policies |
| System Requirements | Compatible with all Operating Systems, including Windows, Mac and Linux Requires USB port (for maximum speeds must be used with a USB 3.0 port) – Backwards compatible with USB 2.0 and 1.1 One gigabyte (GB) = one billion bytes; accessible capacity will be less and actual capacity depends on the operating environment and formatting. |
| Comments | Drive Type: Solid State Drive Encryption: 256-bit AES Hardware Encryption Operating Temperature Range: 5°F to 130°F (-15°C to 55°C) Operating Humidity Range: 95% humidity at temperatures under 131°F (55°C) Vibration: 20G/20-2000Hz Crush Resistant: to 6500 lbs |
Given the transfer rates possible with USB 3.0 (I measured 100MB/s+), it should also be possible to run a virtual machine directly from it as well. I got one for testing, and here are my thoughts:
1. Initial impression: The new Aegis units come in a die-cast alloy enclosure and feel much more rugged than their previous models. This looks and feels like a MIL SPEC device.
2. Ease of setup: Note that each model of Aegis has slightly different instructions. I was initially thrown off by this. A quick trip to the manual download site (don’t just Google it, click through to the proper model!) and I got it sorted. Setting an admin and user password was comparable in difficulty to setting an initial IP on a network printer. You do need to follow the instructions and wait for the proper lights to flash as stated. Also, the indicator lights at the top are chiclet-key shaped and can be mistaken for buttons. Total time: 5min.
3. Compatibility: I did the inital setup and format of the disk on an Ubuntu Linux 14.04 machine with USB and did IO testing on a Windows 9.1 system with USB 3.0. Both systems mounted and unmounted the drive just fine. It appears that no interaction with the OS takes place outside of the usual USB file system operations.
The device was able to host live virtual machines under both VMWare Player and Virtualbox. This makes it suitable for tasks like booting up a PKE server, or getting a backup server on-line as part of a DR exercise.
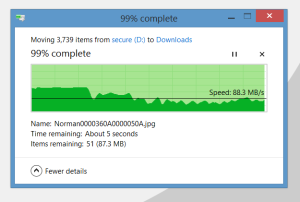
4. Bulk transfer performance: On the USB 2.0 system, large file copies averaged 30MB/sec from an internal OCZ SSD. This is about as good as 2.0 usually gets. Timed file copies on the USB 3.0 system resulted in a much higher average:
Performance hovered at over 100MB/s and was consistently at 80+ for the duration.
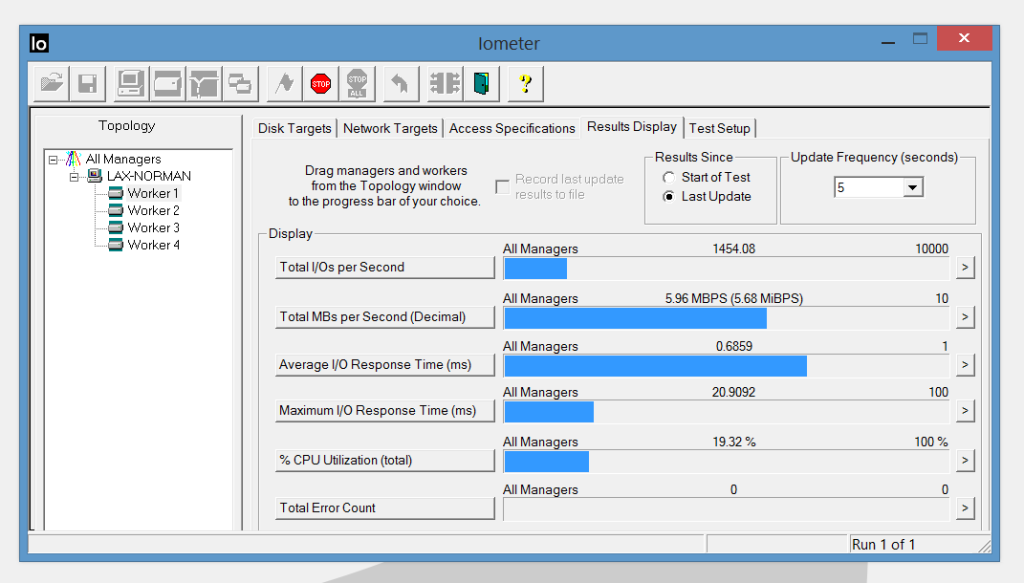
5. Random IO and IOPs: At this point, I decided to run a couple of workloads against the Padlock using Iometer. Here is a 50% read, 50% write test with 0% random access:
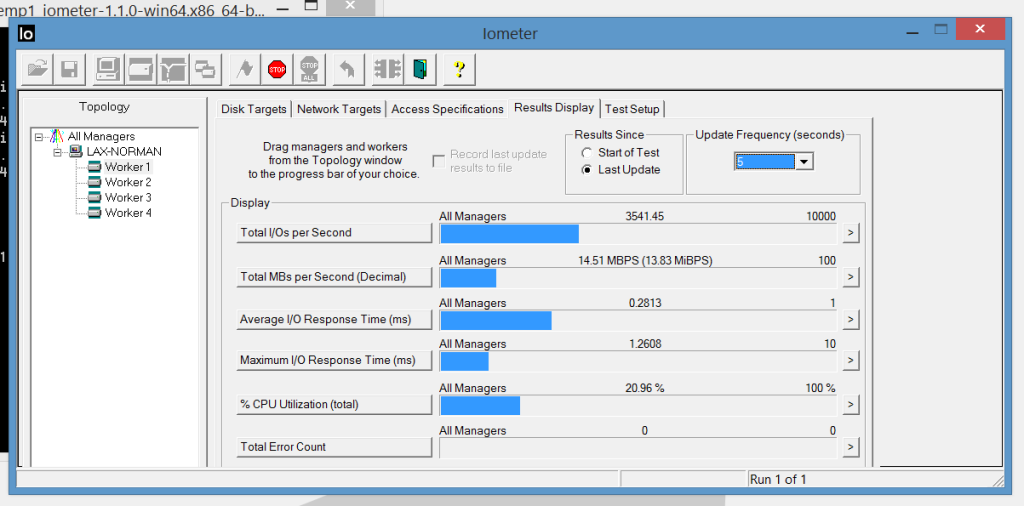
And here it is with the same 50/50 ratio and 100% random access:
This test yielded about 3,500 IOPs and an average seek time under 0.3ms, which is pretty decent for a single USB-attached SSD.
6. Security Features: The new Padlock comes equipped with a laptop-style locking port and a fairly robust case. The encryption keys appeared to be stored in some sort of EEPROM on the electronics package, with the user-selected PIN encrypteing an AES-256 session key used for bulk encryption of the drive. Possible weaknesses include:
- Entropy of the PIN – A user-selectable PIN can be 6-16 digits. At the maximum of 16, this yields approximately 73 bits of entropy (log2(10^16). The firmware does have a scheme to limit brute-force attacks, but this does assume that the encrypted session key cannot be recovered for analysis by some other technical means.
- Human factors- Many users will be tempted to use something obvious, like their office phone number. Sysadmins should be diligent in key selection and counselling when handing these out to field employees. The system also has an auto-lock feature that disconnects the drive after 5-30 minutes of inactivity. This is on by default, but users with admin access could turn it off. The option for a “duress code” that wipes the key material is also user-configurable. This could limit the usefulness of “rubber hose cryptograhpy” although it’s hard to say how many folks would actually take advantage of this. The “look-and-feel” of the device immediately screams “Something important is on here!” and would probably attract unwanted attention at border crossings.
- Fingerprint analysis – cleaning a PIN pad with alcohol or applying UV dye can make frequently-pressed keys obvious under a UV light. Knowing the possible numbers in the PIN reduces the key entropy considerably. Normal wear-and-tear could also reveal PIN information.
- Hardware and firmware analysis – Without a through tear-down and reverse-engineering effort, there is no real way to know how securely the session key is stored, what level of effort would be required to recover and crack it, or if any key material is leaked to disk or over side channels. This is probably the greatest weakness of a hardware-only solution like this: There is really no way to audit it. However, it does have a much smaller attack surface than a general-purpose computer.
Conclusion: This is a convenient, cost-effective solution for cross-platform storage of mobile data. It does have the requisite performance to run software and VMs and it is physically robust. The only disadvantages are its distinctive, MIL SPEC look (if used in some situations) and lack of visibility into the hardware/firmware stack.
February 4, 2015